Drive efficiencies with CI/CD best practices on Amazon Lex
AWS Machine Learning
JULY 7, 2022
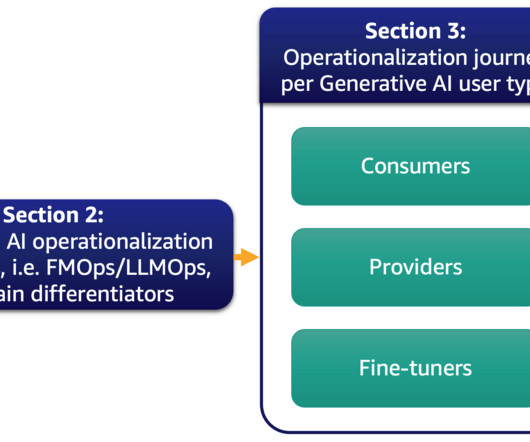
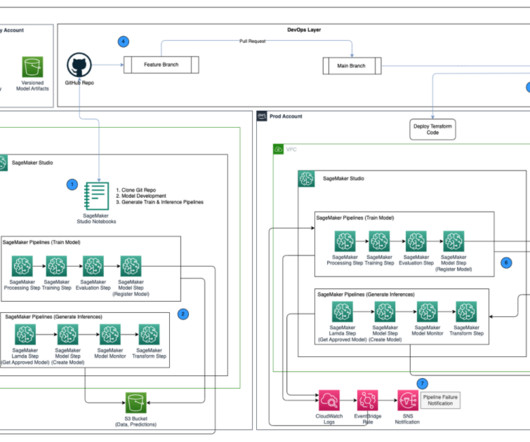
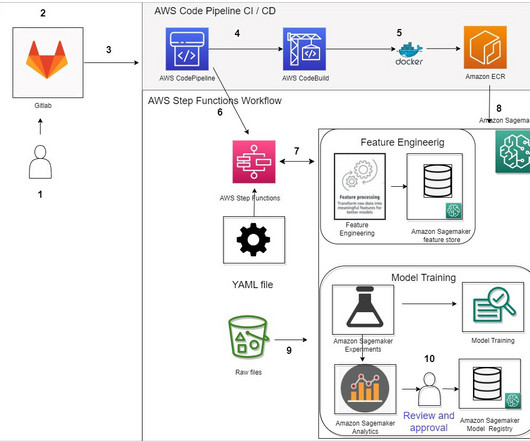
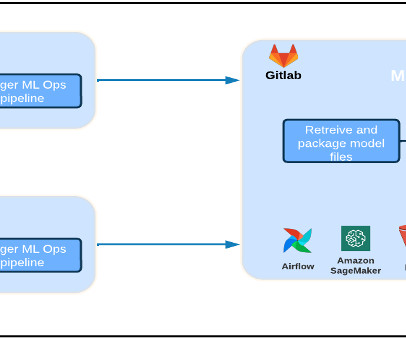
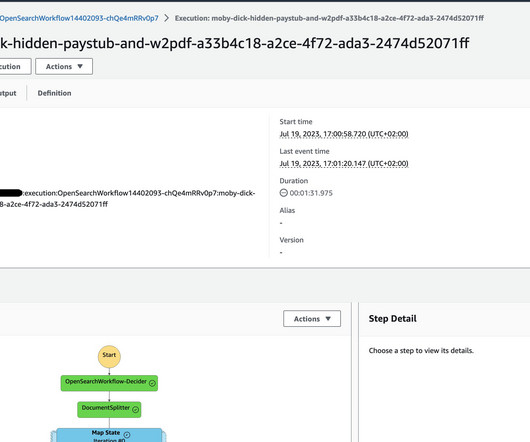
You liked the overall experience and now want to deploy the bot in your production environment, but aren’t sure about best practices for Amazon Lex. In this post, we review the best practices for developing and deploying Amazon Lex bots, enabling you to streamline the end-to-end bot lifecycle and optimize your operations.





































Let's personalize your content