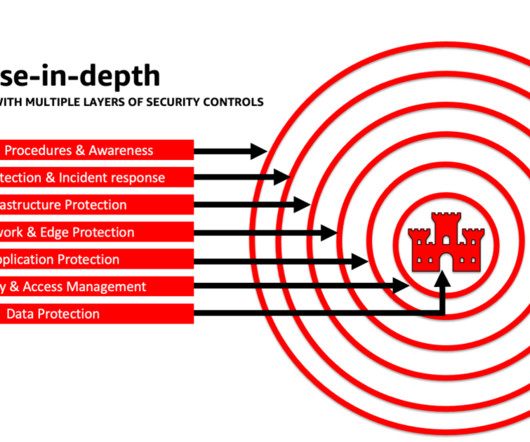
Architect defense-in-depth security for generative AI applications using the OWASP Top 10 for LLMs
AWS Machine Learning
JANUARY 26, 2024
The goal of this post is to empower AI and machine learning (ML) engineers, data scientists, solutions architects, security teams, and other stakeholders to have a common mental model and framework to apply security best practices, allowing AI/ML teams to move fast without trading off security for speed.

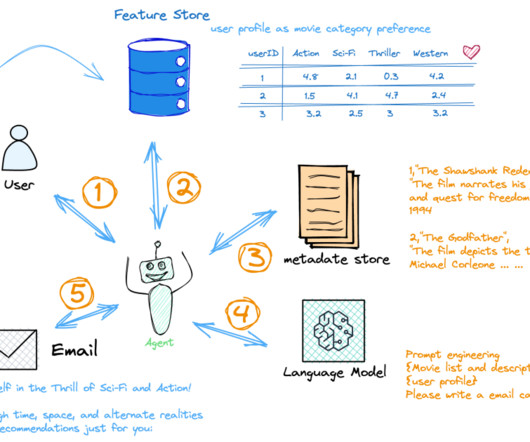








Let's personalize your content