Everything You Need To Know About Stir/shaken
In the present times, a majority of people are facing huge threats from invisible villains that are widely prevalent across the globe. The seemingly innocuous villains are experts at concealing their identities and attack you when you least expect them to. They are robocalls—automated telephone calls that deliver prerecorded messages.
Now, not all robocalls are bad. Many government organizations use them to send important and urgent updates. Several reputable businesses use them to send messages to inform their customers about their products, offers, and deals.
And various marketing and research companies use them to conduct surveys and take feedback. But lately, many scammers and spammers have started employing robocalls for various malicious purposes.
What starts as an irritating phone call can rob you of your identity, and your life’s savings, and do a lot more damage than you can imagine. As per a stat, spam and scam robocalls make up almost 41 percent of total robocall volume.
That means, when Americans received more than 50.3 billion robocalls in 2022 alone, more than 20.6 million robocalls were either scams or spam.

As per the latest data, U.S. customers have received more than 5.46 billion robocalls between January and August 2023, and each person receives about 17 spam calls every day. As per the Federal Trade Commission, robocall scams yielded a median loss of USD 1,400 per person in 2022!
Now the question is, is there a hero that can defeat these ubiquitous supervillains? The answer is a resounding ‘YES!’ Interestingly, a James Bond-esque high-tech tool is fighting against robocalls.
The name is STIR/SHAKEN, which takes inspiration from the famous spy character who prefers his martinis “shaken, not stirred.”
This blog post details everything about STIR/SHAKEN starting from its definition, how it works, adoption in different countries, impact and use cases, challenges, and strategies to overcome the obstacles.
So, without further ado let’s dive right into this in-depth blog and know every relevant thing about STIR/SHAKEN in detail. Read on and thank us later.
What is STIR/SHAKEN in layman’s language?
STIR/SHAKEN (Secure Telephony Identity Revisited/Secure Handling of Asserted information using toKENs) is a caller authentication framework meant to help restore trust by reducing fraudulent robocalls and illegal phone number spoofing.
The foundation of STIR/SHAKEN was laid by Greek-American inventor Ted Paraskevakos in 1968 when he introduced the idea of modem-like devices that would send and receive information over normal voice lines.

The concept was developed in the 1970s. In 1984, the idea got its first public trial with Bell Atlantic and a follow-up in 1987.
In later years, STIR/SHAKEN was developed jointly by the SIP Forum and the Alliance for Telecommunications Industry Solutions (ATIS) to efficiently implement the Internet Engineering Task Force (IETF).
Jointly, STIR/SHAKEN provides a practical mechanism to offer verified information about the caller as well as the origin of the call (known as attestation) for the first time in the network.
To put it simply, STIR/SHAKEN is a feature that ensures callers receive genuine phone calls and not fake and robotic ones. They are service providers with the tools needed to sign and verify calling numbers.
They provide businesses and consumers with the confidence that the calls they receive are from legitimate parties and are safe.
How does STIR/SHAKEN work?
STIR
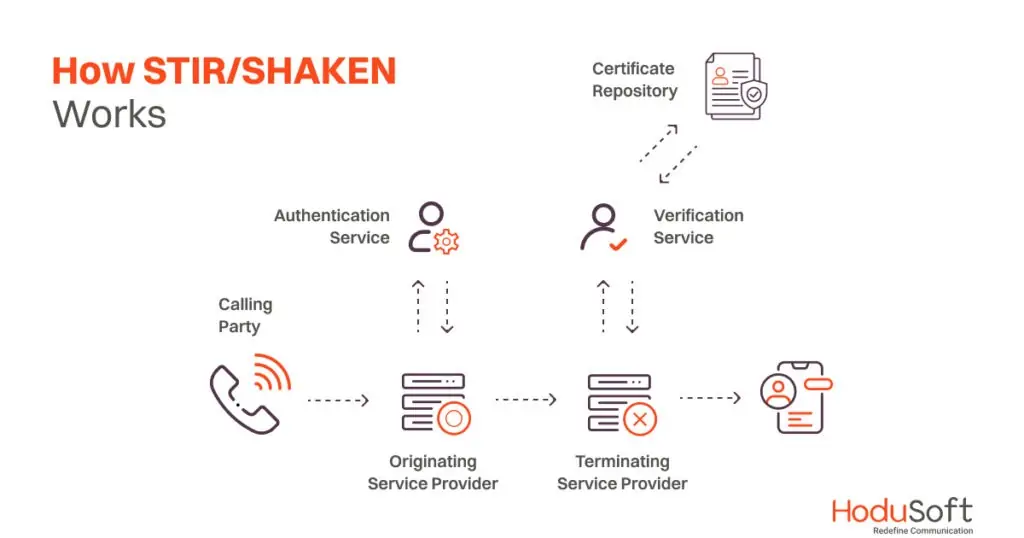
Let’s understand STIR first. The system adds information to the Session Initiation Protocol (SIP) headers, which enables the endpoints to identify the origin of the data. It doesn’t prevent a robocaller’s ability to spoof a caller ID. It, however, enables upstream points to decide if they want to trust that ID or not.
For example, a business phone system using a VoIP-based PBX might connect to the wider telephony network through a SIP service provider. When providers receive the SIP packet, they will add some special information to the call’s details. That information will tell them if they’re sure the call originates from a known source or not.
There are three levels of verification, or “attestation,” how phone companies verify a caller’s identity.
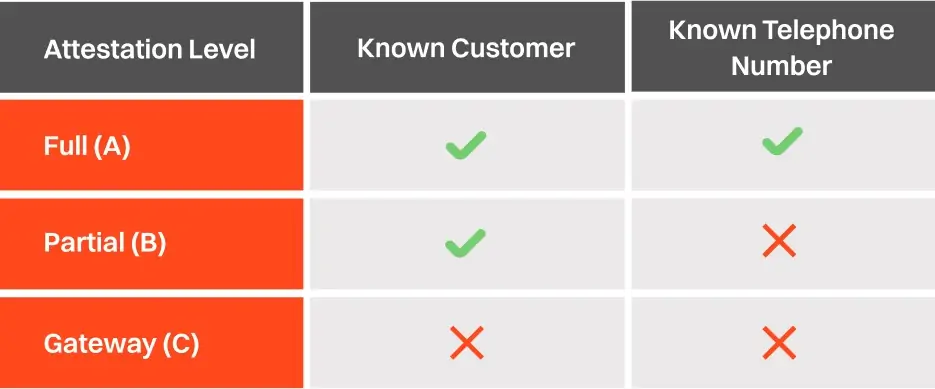
- “A” is the highest level. It means they are sure the caller is who they claim to be. This is like when you call your best friend from your phone.
- “B” is when they’re mostly sure but not completely. Maybe the caller is from a company, and they know the company but not the specific person.
- “C” is the lowest level. It means they only know that the call is coming from a particular place, like a company’s phone system.
To make sure this information stays safe, the providers put it in a special digital envelope called JSON Web Token. This envelope contains details such as:
- The originating phone number as provided by the original SIP
- A number being called
- The level of attestation provided by the provider
The provider’s private key encrypts and the public key decodes the STIR information. If anyone fails, the information is regarded invalid.
SHAKEN
Like STIR, SHAKEN is based on SIP and is designed to work with calls being routed through a VoIP network. It is like a special code for phone calls to make sure they’re from the right person. But it only works with certain kinds of phones, not the old ones.
SHAKEN helps check if the call is real and not pretending to be someone else when it’s in the special internet phone part. But once it gets into the regular phone network, it’s like going into a dark tunnel where SHAKEN can’t help anymore.
Also, if SHAKEN finds a call is fake, it can’t just stop the call because that would be a problem. So, they’re still figuring out how to tell people if a call is a spam or scam robocall adequately.
Enforcement of STIR/SHAKEN in different countries
In January 2018, the Canadian Radio-television and Telecommunications Commission (CRTC) issued Compliance and Enforcement and Telecom Decision 2018-32, which states that the CRTC expects Canadian Telecommunications Service Providers to adopt STIR/SHAKEN by March 31, 2019, establish a Canadian administrator, and issue progress reports.

In December 2019, the CRTC extended the deadline to September 30, 2020. In 2020, they extended the deadline to November 30, 2021. The commission also approved the establishment of the Canadian Secure Token Governance Authority (CSTGA) as the Governance Authority for STIR/SHAKEN.
When it comes to the United States, STIR/SHAKEN is a major ongoing effort of the Federal Communications Commission. The commission inked the Telephone Robocall Abuse Criminal Enforcement and Deterrence Act, which mandates the use of the protocols by June 30, 2021, for large carriers and by June 30, 2022, for smaller and rural carriers.
Impact of STIR/SHAKEN
STIR/SHAKEN is an important tool to improve call authenticity and reduce the impact of fraudulent and unwanted calls in the telecommunications industry. So, unsurprisingly it has many use cases. Here are some of them:
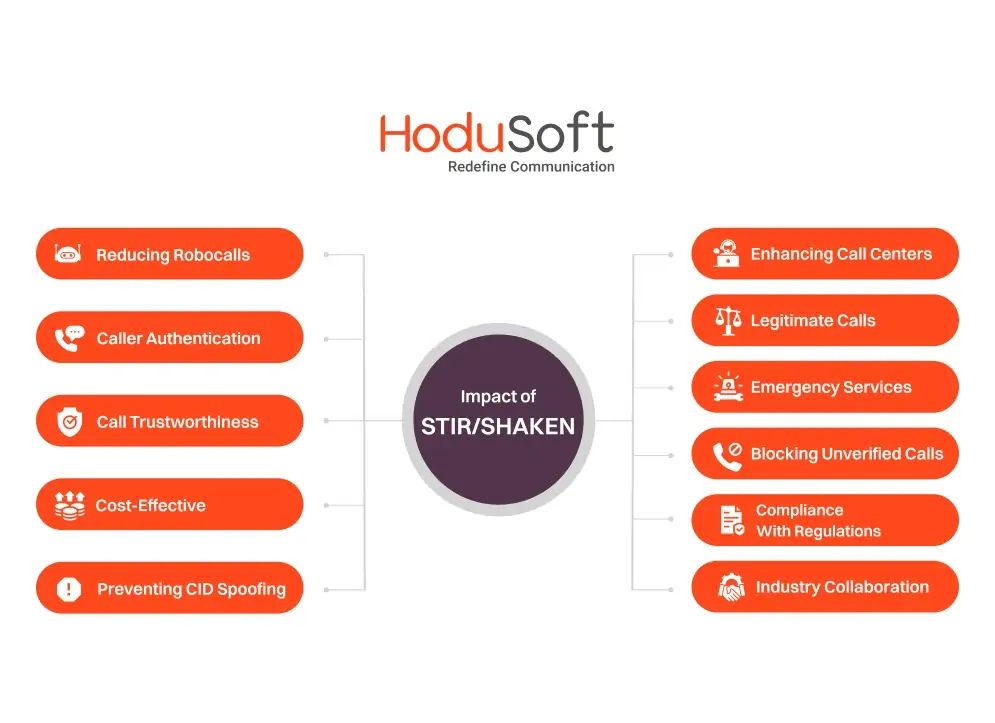
1. Reducing robocalls
The very purpose of the STIR/SHAKEN feature is to identify and block robocalls. When unscrupulous parties started ‘spoofing,’ a technique to hide the true origins of a call and prevent callbacks. When it became extremely common, the feature empowered individuals and organizations to fight robocalls and arrest spoofing.
2. Caller authentication
STIR/SHAKEN feature verifies the caller’s identity. It matches the caller information displayed and the actual number from which the call originates. By doing so, it allows users to trust the caller’s identity. When the caller’s identity is authenticated, the receiver can take the call without any worry.
3. Call trustworthiness
Would you trust the incoming calls if you keep on receiving scams and spam calls day in, and day out? No. That’s where the STIR/SHAKEN feature helps in building trust. When phone numbers are identified and are authorized to be received, they improve call trust and ensure users can receive all incoming calls with confidence.
4. Cost-effective
STIR/SHAKEN can be cost-effective by reducing fraudulent calls and ensuring that users can avoid costly scams. Apart from that, the allowed incoming calls from conventional phone equipment massively reduce costs as they don’t need callers to use long-distance telephone service.
5. Preventing caller ID spoofing
As discussed previously, unscrupulous and malicious people rely on caller ID spoofing to hide call origins and impersonate other people. However, the STIR/SHAKEN feature prevents caller ID spoofing. When malicious callers are barred from spoofing caller IDs, the cases of fraud and impersonation are considerably reduced.
6. Enhancing call centers
Since its inception, the STIR/SHAKEN feature played a huge role in boosting call centers. Call centers not only use STIR/SHAKEN to verify their identity but also to improve their outbound call performance. The tool also allows them to give their customers the confidence that they are dealing with the right call centers and don’t have to worry about robocalls and fraudulent calls.
7. Legitimate calls
Some sectors, such as healthcare or finance, benefit from STIR/SHAKEN more than other sectors. When people’s health, wealth, and well-being are at stake in these sectors, companies operating in these industries do whatever it takes to make sure their important calls are not blocked or ignored.
8. Emergency services
As discussed in the introduction, not all robocalls are bad. Many government institutions use them to relay urgent and important information. If emergency messages and calls are flagged and not allowed to pass, then it can cause huge problems. Here the STIR/SHAKEN feature can come in extremely handy. Emergency services can leverage the feature to make sure that their calls reach the intended recipients in situations where quick response is vital.
9. Blocking unverified calls
Unverified calls can be extremely dangerous for big businesses and high-networth individuals (HNIs). Just one unverified call made with malicious intent can act as a Trojan Horse and endanger the wealth, security, and credibility of an entire organization or individual. STIR/SHAKEN can help service providers block unverified calls as well as label them as potentially fraudulent.
10. Compliance with regulations
Would it surprise you to know that STIR/SHAKEN helps service providers to comply with legal and regulatory requirements? They indeed do that by enabling telecom companies to abide by all the regulations related to caller ID verification and spam call prevention. Businesses can ensure that calls made on their behalf have their legitimate caller ID.
11. Industry collaboration
Did you know that the implementation of STIR/SHAKEN has fostered collaboration within the telecommunications industry? Since the widespread adoption of STIR/SHAKEN as well as the government mandate in the US and Canada, many service providers, carriers, and regulators are working closely together to establish a more secure and trustworthy calling ecosystem.
Challenges of STIR/SHAKEN
Even though STIR/SHAKEN is a promising technology for addressing caller ID spoofing and improving call authenticity, it faces some unique challenges. Here we are not only going to discuss the challenges but also going to list the solutions using which they can overcome the challenges.
1. Limited adoption
As of now STIR/SHAKEN is mainly implemented in the US and Canada. Expanding its adoption globally is challenging due to differences in regulatory environments, technical infrastructure, and standards among countries.
Implementing STIR/SHAKEN for international calls requires cooperation between different countries and their respective regulations and standards. All these factors make it a complex and ongoing process.
2. Cost and complexity of implementation
Implementing STIR/SHAKEN can be expensive for smaller service providers and carriers, as it requires investments in new equipment and infrastructure. These service providers may find it expensive to procure the necessary infrastructure and obtain digital certificates, potentially leading to disparities in adoption. These costs may be passed on to consumers.
Integrating STIR/SHAKEN into existing telecommunications networks can be complex, especially for older systems. It may require significant changes and updates to network infrastructure.
3. Deployment across networks
One of the primary challenges is the need for universal adoption across diverse telecommunication networks.
STIR/SHAKEN’s effectiveness relies on widespread implementation, and smaller or older networks may face hurdles in adopting the framework.
4. Robocallers and fraudsters: Spoofing Beyond Caller ID
As technology evolves, so do the tactics used by scammers and fraudsters. Determined fraudsters will always find ways to spoof caller IDs—either through networks that don’t implement STIR/SHAKEN or by manipulating the system.
Malicious actors can still use other methods, such as social engineering, to deceive users and commit fraud. STIR/SHAKEN must adapt to new threats and challenges to remain effective.
5. Legitimate caller ID changes
Businesses and individuals often change their caller ID information for valid reasons, and the framework must accommodate these changes without causing disruptions.
STIR/SHAKEN is not perfect and can produce false positives and negatives. Legitimate calls may be flagged as fraudulent (false positives), while some fraudulent calls may still get through (false negatives).
6. Consumer education
Even with STIR/SHAKEN, users need to be educated about interpreting attestation levels and how to respond to calls with different levels of trust.
Even with STIR/SHAKEN in place, consumers must be educated about the technology and understand how to use it effectively to avoid scams and fraudulent calls.
Ways to overcome challenges associated with STIR/SHAKEN
While there are challenges, there are also ways to mitigate those. Here are some of the ways:
- Regulatory initiatives: Regulatory bodies like the FCC in the United States have mandated the implementation of STIR/SHAKEN, which encourages service providers to comply and adopt the framework.
- International collaboration: Efforts are underway to establish international agreements and standards for cross-border STIR/SHAKEN implementation, making it more effective in combating international robocalls.
- Collaboration with reliable and reputable technology providers: Working with reliable and reputable technology providers such as HoduSoft, to incorporate STIR/SHAKEN support can further bolster its effectiveness. At HoduSoft, we understand how important it is to implement STIR/SHAKEN to safeguard both the company’s reputation and its customers’ interests.
- Consumer education: Even though STIR/SHAKEN has been around for a while, it is still not known to many individuals and businesses. Although many people and companies are tired of robocalls and are looking for effective solutions to fight the menace, they don’t have much idea about the feature. Public awareness campaigns and educational efforts aim to help users understand the new call trust indicators and empower them to make informed decisions.
- Innovation and security measures: Ongoing research and development work on STIR/SHAKEN aims to enhance its security features, adapt to evolving threats, and address emerging challenges.
Taking everything into account,
Engineered to fight the growing menace of scams and spam robocall calls, STIR/SHAKEN is one of the most important innovations in the telecommunication sector in recent times. The STIR/SHAKEN not only verifies every caller’s identity but also provides a robust cryptographic signature for each call.
At HoduSoft, we have designed a robust STIR/SHAKEN compliant IP PBX System that ensures all regulatory compliance and eliminates the risk of spam and scam calls. If you want to know more about our STIR/SHAKEN framework, contact us today to get a free demo.



